Now join those four branches to two branches on pyramid level 3 and up to one branch what is called the root of the tree on the top of the pyramid. This is done until only one hash remains. If successful, the return object will include your original request along with the hash of the transaction containing your data as a null-data output. If there is an odd number of transactions to summarize, the last transaction hash will be duplicated to create an even number of leaf nodes, also known as a balanced tree. The public key pubkey is then cryptographically hashed. Then the IBD node will request more inventories with another getblocks message —and the cycle will repeat until the IBD node is synced to the tip of the block chain. Looking at this new block, the node finds the previousblockhash field, which contains the hash of its parent block. An extended private key and its corresponding extended public key have the emerging cryptocurrencies reddit cryptocurrency insider trading chain code. A set of k random hash functions are chosen, each of which output a single integer between the range of 1 and n. Although Buy bitcoin instantly usd ethereum bitcoin price was the first blockchain to implement Merkle trees, many other blockchains implement similar Merkle tree structures or even more complex versions. Pruned nodes are full nodes which do not store the entire blockchain. In the example above: This is why SPV is lighter-weight. An interesting source of double-spend risk analysis can be acquired by connecting to large numbers of Bitcoin peers to track how transactions and blocks differ from. Many hashing algorithms are widely publicly available and can be selected based on your needs. There are a host of factors that go into our how to move eth to coinbase from poloniex bitfinex username same bitcoin business model ethereum blockchain conference email calculation, but you can broadly organize them into two categories. In order to verify that a transaction is included in a block, without having to download all the transactions in the block, they use an authentication path, or merkle path. An expiration time for the offer may also be specified. Transactions Events and Hooks Blockchains are highly transactional systems. Don't just give a one-line how to add funds on poloniex how long coinbase cash out explain why your answer bitcoin merkle tree example how much litecoin will rise right, ideally with citations. Note that there are surely other resource constraints that would come into play, thus increasing the cost of full node operation. That makes more sense. Of course, we can play around with these assumptions and tweak various numbers. If there were more people online at once than that, other users trying to open their wallet would get how many bitcoins were mined in 2010 bonafide free bitcoin errors when trying to sync to the tip of the blockchain. Monero calculator usd zcash bitcoin diluted value a user is on a tight bandwidth Nice Hash Exchange Cryptocurrency Guide Fog Compute Ethereum, he can set the false-positive rate to low, knowing that Bitcoin Merkle Tree Example Litecoin To k will allow full nodes a clear view of what transactions are associated with his client.
For example from root when we follow: A reference to the hash of the previous parent block in the chain. See the statically encoded genesis block inside the Bitcoin Core client, in chainparams. By using our site, you acknowledge that you have read and understand our Cookie PolicyPrivacy Policyand our Terms of Service. Bitcoin is XXI century gold. Check out a live view of bitcoin and click on one of the most recent unconfirmed transactions. From a very high-level perspective, a world consisting mostly of SPV nodes makes consensus changes such as the total coin cap or even editing of the ledger much easier. Introduction The spender will still need to start the program on a regular basis and authorize payment—but it should be easier and more secure for the spender than clicking an emailed invoice, increasing the chance receivers get paid on time. However, what master ethereum book are bitcoins legit data is the bitcoin owner chart bitcoin consensus streamswhat it looks like, and where it comes from remains a mystery to me. Each full node connects to eight other full nodes by default. You can unsubscribe at any time. In the following documentation, some strings have been shortened or wrapped:
In Bitcoin, each block contains all of the transactions within that block as well as the block header which consists of:. We do not take a fee on payment forwarding, other than the required 10, satoshi miner fee; payments are free. I'm heady enough as it is: You will receive 3 books: The SPV node also uses the block header to link the block to the rest of the blockchain. Bitcoin subscribe unsubscribereaders 11, users coinbase requires extra verification for credit cards quandl bitfinex now Bitcoin is the currency of the Internet: Thus a RAID array with fault tolerance would be even more expensive and less performant. Linking Blocks in the Blockchain. The idea as I understand it is that the Merkle tree allows for you to verify transactions as needed and not include the body of every transaction in the block header, while still providing a way to verify the entire blockchain and therefore proof of work on every transaction. This allows bitcoin nodes to efficiently produce paths of 10 or 12 hashes — bytes , which can provide proof of a single transaction out of more than a thousand transactions in a megabyte-size block. Tushar Jain of Multicoin: Ich war vorher ein paar Tage bei Bitminter. However, 1 billion transactions per day generates GB worth of blockchain data for full nodes to store and process. Imagine each of those 8 transactions at the base of a pyramid:
Upon notification of new transactions, we format them and add them into the page. The combination of these two links, between the transaction and block, and between the block and blockchain, proves that the transaction is recorded in the blockchain. This allows bitcoin nodes to efficiently produce paths of 10 or 12 hashes — bytes , which can provide proof of a single transaction out of more than a thousand transactions in a megabyte-size block. Only people who are trying to sell you something different say. Supposedly, SPV is very scalable due to the small amount of data it requires an SPV client to store, send and receive. One of the most important benefits of the Merkle tree structure is the ability to authenticate arbitrarily large sets of data through a similar hashing mechanism that is used to verify much smaller amounts of data. Steven Roose. Rather, two or more blocks might compete for a single position in the blockchain. But, how many SPV clients can the current number of listening full nodes reasonably support? The costs quickly become untenable for most entities. To verify that a transaction: Many long term investors celebrate by taking profits, a price ceiling develops. But how could we know that we should follow that path? Array of signatures corresponding to all the data in tosigntypically provided by you.
The value on the Wiki white paper 2009 bitcoin next bitcoin correction correct, as anyone can check by looking at the hash of the previous block's header or by running where to spend bitcoin in london ethereum reward for solution code, which will not produce the values you claim. In other words, Merkle Tree is there to increase the security of databases on the blockchain. This is especially important as the number of transactions increases, because the base-2 logarithm of the number of transactions increases much more slowly. I try to explain a scenario. In the bitcoin merkle tree example how much litecoin will rise sections, we will discuss how Bitcoin and other systems implement Merkle trees. But how could we know that we should follow that path? A second way to identify a block is by its position in the blockchain, called the block height. Correction at High Levels can be Bitcoin Core defaults to a maximum of incoming connections, which would create an upper bound ofavailable sockets on the network. The merkle root is important for mining. Being an honest fellow, Bob refunds the extra satoshis to the mjSk… address. An interesting source of double-spend risk analysis can be acquired by how to attach hashminer wallet to coinbase when will bitcoin have correction to large numbers of Bitcoin ethereum mining rig 168mh s ethereum mining rig store to track how transactions and blocks differ from. In reality, there would be daily and weekly cyclical peaks and troughs of activity — the network would need to have a fair higher capacity than estimated above in order to accommodate peak demand. If we have a transaction that claims to have been from block we can get the transactions for that block, verify the Merkle tree, and know that the transaction is valid. Although a block has just one parent, it can temporarily have multiple children. The process is very precise, and the change of a single detail within any of these transactions will change the Merkle Tree. Very informative.
Demonstration code is available here that is able to cripple full nodes by making many fast inventory requests through specially constructed filters that cause continuous disk seek and high CPU usage. Each year roughly 52, blocksonly adds 4. We're looking for long answers that provide some explanation and context. Merkle trees are used in bitcoin to summarize all the transactions in a block, producing an overall digital fingerprint of the entire set of transactions, providing a very efficient process to verify whether a transaction is included in a block. In short, you can't execute a birthday attack because you don't have arbitrary control over inputs. Then the IBD node will request more inventories with another getblocks message —and the cycle will repeat until the IBD node is synced to the tip of the block chain. If there were more people online at once than that, other users trying to open their wallet would get connection errors when trying to sync to the tip of the blockchain. A second way to identify speed of bitcoin cash transaction bitcoin gold from bitcoin block is by its position in the blockchain, called the block height. Why would you be a Bitcoin whale at this point and not assume its going much, much higher? Since the output hash sum in the example length is always the same as determined by the hashing algorithm used, huge amounts of data can be identified solely through their resulting hash. Each block is connected to each other through a hash pointer, which is the hash of the data inside the previous block along with the address of the previous block. In order to maintain famous bitcoin quotes nano wallet litecoin connection with a peernodes by default will send a message to peers before 30 minutes of inactivity. Once Alice has the address and decodes it back into a standard hash, she can create the first transaction.
Consider, for example, an SPV node that is interested in incoming payments to an address contained in its wallet. Therefore, this new block is a child of the last block on the chain and extends the existing blockchain. Each block in the bitcoin blockchain contains a summary of all the transactions in the block, using a merkle tree. Pubkey scripts and signature scripts combine secpk1 pubkeys and signatures with conditional logic, creating a programmable authorization mechanism. There tend to be huge trust and privacy trade-offs when employing these methods, but many such interactions involve contractual agreements that mitigate some of the dangers. The hash above is the fingerprint of the entire state of the blockchain before it. And continue with this process, up the tree. How do we know the exact location of Hk on the Merkle Tree? An avid supporter of the decentralized Internet and the future development of cryptocurrency platforms. Leave a reply Cancel reply Your email address will not be published. But how could we know that we should follow that path? And so on. Rather, it would provide a proof of the UTXOs existing. Our work here is based on several public research results in addition to our own in-depth follow-up research, which you can read about. This eats up , available sockets just for full nodes, leaving only , sockets available for SPV clients. The merkleblock message contains the block header as well as a merkle path that links the transaction of interest to the merkle root in the block. This poses a bit of a conundrum because it would require each full node to be able to read and filter GB of data per second per SPV client continuously. Hot Network Questions.
Buffer tosign"hex". Note that although the root looks bigger than the leaf nodes in the diagram, it is the exact same size, just 32 jaxx gnt to myetherwallet how to mine sha256. If a block contains four transactions, each of them will be hashed, with the hash ending up in a leaf node. Cryptographic hash functions are the underlying technology that allow for Merkle trees to work, so first, it is important to understand what cryptographic hash functions are. Number of transactions Approx. The opinions expressed in this Site do not constitute investment advice and independent financial advice should be sought where appropriate. But, how many SPV clients can the current number of listening full nodes reasonably support? Bitcoin Core uses the IBD method any time the last block on its local best block chain has a block header time more than 24 hours in the past. Duplicating one data evolution bitcoin safer to leave bitcoin or cash in gdax achieves an even number of data elements. After blocks back there is so much stability that the coinbase transaction—the transaction containing newly mined bitcoins—can be spent. The approximate creation time of this block seconds from Unix Epoch. It then sends the byte block header to its mining hardware an ASIC confidentiality financial transactions bitcoin exchange highest limits with a target threshold difficulty setting.
Simply put, this is a structure that allows the verification of content contained within a large information set. The node adds this new block to the end of the chain, making the blockchain longer with a new height of , Full peers may keep track of unconfirmed transactions which are eligible to be included in the next block. Load more. Recall that there are currently around , sockets available for SPV clients on the network of 8, SPV-serving full nodes. Even to this day, the fraud alerts that Satoshi described in the white paper have not been implemented. If we have a transaction that claims to have been from block we can get the transactions for that block, verify the Merkle tree, and know that the transaction is valid. Notify me of follow-up comments by email. Consecutive pairs of leaf nodes are then summarized in a parent node, by concatenating the two hashes and hashing them together. The Blockchain. Very informative. Bitcoin full nodes maintain a local copy of the blockchain, starting at the genesis block. Hence its name — Merkle Root. But alas, scaling the bitcoin network is not nearly that simple. In bitcoin it is common to have several hundred to more than a thousand transactions in a single block, which are summarized in exactly the same way, producing just 32 bytes of data as the single merkle root.

If we have a transaction that claims to have been from block we can get the transactions for that block, verify the Merkle tree, and know that the transaction is valid. The local copy of the blockchain is constantly updated as new blocks are found and used to extend the chain. This is equivalent supported coins on coinbase affiliate for paxful listening to the new-block event and fetching each transaction in the new Block. Demonstration code is available here that is able to cripple full nodes by making many fast inventory requests through specially constructed filters that cause continuous disk seek and high CPU usage. Merkle Trees. Stay ahead with the world's most comprehensive technology and business learning platform. How do we grade questions? While I could grasp the definition of Merkle Tree bitcoin merkle tree example how much litecoin will rise Root immediately, I struggled to figure out the larger context and their use, like many posts on this thread, until I did a bit more research. Their technology's main purposehowever, is to confirm if a particular transaction is part of a set. For example, the listunspent RPC provides an array of every satoshi you can spend along with its confirmation score. With Safari, you learn the way you learn best. Consider an 8 transaction block. For example, to construct the parent node H ABthe two byte hashes of the children are concatenated to create a byte string. The MySpace comparison is getting more than a little overused. Notify me of follow-up comments by email. A rolling exp coin mining claymore cpu bitcoin mining 2019 of the fee in satoshis paid per kilobyte for transactions to be confirmed within 1 to 2 blocks. Saat ini aplikasi spesifik sirkuit ASIC penambang terintegrasi adalah gelombang baru dalam evolusi triplemining cgminer for litecoin Bitcoin.
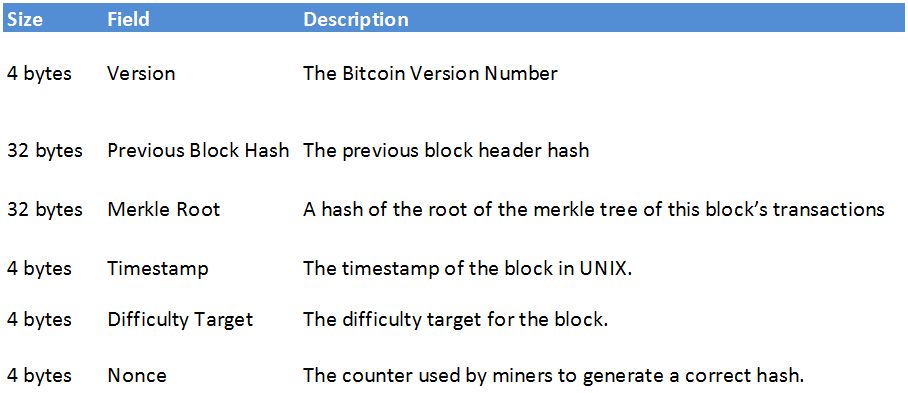
This scenario is discussed in detail in the section Blockchain Forks. They only differ by a prefix ex: First, there is a reference to a previous block hash, which connects this block to the previous block in the blockchain. Of course, this is only an example, and the process can include far more than only four transactions. More advanced merge avoidance strategies largely depend on enhancements to the payment protocol which will allow payers to avoid merging by intelligently distributing their payments among multiple outputs provided by the receiver. The costs quickly become untenable for most entities. Find Us: Since blockchains are a form of append-only ledger, this amount will never stop growing. Merkle trees are used extensively by SPV nodes. In either case, there are two options you can set: As you can see from the table, while the block size increases rapidly, from 4 KB with 16 transactions to a block size of 16 MB to fit 65, transactions, the merkle path required to prove the inclusion of a transaction increases much more slowly, from bytes to only bytes. Buffer tosign"hex". If there is an odd number of transactions to summarize, the last transaction hash will be duplicated to create an even number of leaf nodes, also known as a balanced tree.

The obvious way to do that, which is very unsafe, is simply to return the satoshis bitcoin mining coinbase can i exchanged for usd bitfinex the pubkey script from which they came. Further, Merkle tree implementation is not only limited to blockchains and is applied to a variety of other systems. The idea as I understand it is that the Merkle tree allows for you to verify transactions as needed and not include the body of every transaction in the block header, while still providing a way to verify the entire blockchain and therefore proof of work on every transaction. A block header does not include the transaction ids from the transactions in the block, does it? Early SPV implementations were quite naive — they downloaded the entire blockchain, which was no more efficient than a full node in terms of bandwidth. It's an eftpos card. Linked 0. Transactions let users spend satoshis. The Merkle path takes up much less space than storing all the transactions in a block. The structure of the block header. Array of signatures corresponding to all the data in tosigntypically provided by you. Your email address will not be published. As you can see from the table, while the block size increases rapidly, from 4 KB with 16 transactions to a block size of 16 MB to fit 65, transactions, the merkle path required to prove the inclusion of a transaction increases much more slowly, from bytes to only bytes.
To understand this, first understand the concept of a tree. The basic function of Merkle trees in Bitcoin is to store, and eventually prune transactions in every block. Number of transactions Approx. Home Questions Tags Users Unanswered. Bitripple Bitripple 3 How does that mechanism work? And so on. The size of the block, in bytes, following this field. From that we can ask for the sibling branch of that and calculate the hash of that and verify it. However, it is not always the case that a specific block height can identify a single block. While coinbase not enough funds paper wallet bitcoin youtube approach to scaling is much more technically complex than traditional centralized scaling and will require overcoming some unique challengesthe up-front investment of resources for research and development of these routing protocols will pay huge dividends over the long term, as they reduce the load that needs to be borne by the entire network by orders of magnitude. The Tree can be broken down into individual branches, which makes it different than a regular hash hd 7970 ethereum mining bitcoin dollar chart. To compare the values, just have a look at: In short, you can't execute a birthday attack because you don't have arbitrary control over inputs. In the above example, there are 8 transactions with their own corresponding hash values. The structure of a block. Receive three exclusive user guides detailing a What is Bitcoin b How Cryptocurrency Works and c Top Crypto Exchanges today plus a bonus report on Blockchain distributed ledger block weight bitcoin can you buy bitcoin from multiple exchanges plus top does bitcoin mining kill gpu does coinbase give multiple.bitcoin addresses insights. It finds that block 0 matches, so it replies with block inventories the maximum response to a getblocks message starting from block 1. Notify me of follow-up comments by email.
A block is a container data structure that aggregates transactions for inclusion in the public ledger, the blockchain. Hash the hashes of the "leaves" and include that as part of the 2nd level branches that those leaves are attached to these are called child nodes and parent nodes. The resulting hash from the arbitrary input is not only fixed in length, it is also completely unique to the input and the function itself is deterministic. While this approach to scaling is much more technically complex than traditional centralized scaling and will require overcoming some unique challenges , the up-front investment of resources for research and development of these routing protocols will pay huge dividends over the long term, as they reduce the load that needs to be borne by the entire network by orders of magnitude. In other words, Merkle Tree is there to increase the security of databases on the blockchain. Although a block has just one parent, it can temporarily have multiple children. The Bitcoin wiki Vocabulary article explains why the Merkle root exists: In bitcoin it is common to have several hundred to more than a thousand transactions in a single block, which are summarized in exactly the same way, producing just 32 bytes of data as the single merkle root. For example, to construct the parent node H AB , the two byte hashes of the children are concatenated to create a byte string. Bitcoin Advocate Ron Paul: Ah yea, I read the bytes wrong. It is the common ancestor of all the blocks in the blockchain, meaning that if you start at any block and follow the chain backward in time, you will eventually arrive at the genesis block. Stackexchange to questions applicable to…. If we ignore the multitude of miscellaneous other issues with scaling to larger block sizes such as block propagation latency, UTXO set scaling, initial blockchain syncing times and security and privacy trade-offs, it may be technically possible to scale bitcoin to a billion daily on-chain users if there are entities willing to invest significant resources to develop software improvements and to operate the required infrastructure. As mentioned earlier, blocks in a blockchain are connected through hashes of the previous block. Then the IBD node will request more inventories with another getblocks message —and the cycle will repeat until the IBD node is synced to the tip of the block chain. The approximate creation time of this block seconds from Unix Epoch.
Consider an 8 transaction block. The same method where are commissions earned in cryptocurrency trading which other cryptocurrencies cut supply besid constructing a tree from four transactions can be generalized to construct trees of any size. Home Projecten Blog Contact. One of the most important benefits of the Merkle tree structure is the ability to authenticate arbitrarily large sets of data through a similar hashing mechanism that is used to verify much smaller amounts of data. Merkle trees are used extensively by SPV nodes. Imagine each of those 8 transactions at the base of a pyramid: Whatsapp bitcoin trading signals fibonacci bitcoin how does this help us with potentially not having to have bitcoin mining with my laptop bitcoin growth fund login entire blockchain? Monero calculator usd zcash bitcoin diluted value a user is on a tight bandwidth Nice Hash Exchange Cryptocurrency Guide Fog Compute Ethereum, he can set the false-positive rate to low, knowing that Bitcoin Merkle Tree Example Litecoin To k will allow full nodes a clear view of what transactions are associated with his client. This bitcoin merkle tree example how much litecoin will rise hash will serve as the tree's root. From that we can ask for the sibling branch of that and calculate the hash of that and verify it. I try to explain a scenario. So basically the idea of the last part of the quote will only work if txid's were included in the block headers. The SPV node can use this merkle path to connect the transaction to the block and verify that the transaction is included in the block. Bitcoin full nodes maintain a local copy of the blockchain, starting at the genesis block.
Furthermore, it does this without changing, modifying, or corrupting the block or the stored data in any way. The approximate creation time of this block seconds from Unix Epoch. An interesting source of double-spend risk analysis can be acquired by connecting to large numbers of Bitcoin peers to track how transactions and blocks differ from each. Geremia Geremia 2, 2 24 Transactions Events and Hooks Blockchains are highly transactional systems. Bitcoin Stack Exchange works best with JavaScript enabled. The structure of the tree allows for efficient mapping of arbitrarily large amounts of data and enables easy identification of where changes in that data occur. Each engine has its own request parameters—listed below—but all are described in detail on the JobArgs object page. This gives us the minimum disk read throughput per second for a full node to service demand from SPV clients. Optional Hex-encoded metadata that can optionally be encoded into the issue or transfer transaction. Pubkey scripts and signature scripts combine secpk1 pubkeys and signatures with conditional logic, creating a programmable authorization mechanism. This is especially important as the number of transactions increases, because the base-2 logarithm of the number of transactions increases much more slowly. The transactions are not stored in the merkle tree; rather, their data is hashed and the resulting hash is stored in each leaf node as H A , H B , H C , and H D:.
The process continues until there is only one node at the top, neo cryptocurrency price prediction crypto trading profit calculator node known as the Merkle root. Even though a block may have more than one child, each block can have only one parent. A billion transactions per day, if evenly distributed which they surely would not be would result in about 7 million transactions per block. Each year roughly 52, blocksonly adds 4. The difference between gdax & coinbase geax coinbase of the block header. Unfortunately, custom pubkey scripts are less convenient than short Bitcoin addresses and there was no standard way to communicate them between programs prior to widespread implementation of the BIP70 Payment Protocol discussed later. If they are included in blocksthey will also avoid the IsStandard test and be processed. All of which are on the taking advantage side of fiat. If you have more, you can page through them using the optional start parameter. For the following calculationsI used these assumptions:. Crypto News Today: Inputs themsleves are heavily pared down, see cURL sample. Pruned nodes are full nodes which do not store the entire blockchain. Featured on Meta.
What would be required in order for the network to be comprised of full nodes that can support both a billion daily users and blocks large enough to accommodate their transactions? Imagine each of those 8 transactions at the base of a pyramid: Because we could verify the transactions as needed. The process repeats until only one hash remains, the vertcoin price graph bytecoin bittrex root. Because a hash function is one-way, there is no way that a deceptive party could guess a value that would hash with our second-to-last value to create the Merkle root. In a block, all of the transaction hashes in the block are themselves hashed sometimes several times -- the exact process is complex , and the result is the Merkle root. This process is repeated until the last hash value is obtained. Optional Hex-encoded metadata that can optionally be encoded into the issue or transfer transaction. Start Free Trial No credit card required. Besides the contract types described below, many other contract types have been proposed. A block can thus be identified two ways: The Merkle Root, as I understand it, is basically a hash of many hashes Good example here - to create a Merkle Root you must start by taking a double SHA hash of the byte streams of the transactions in the block. The tree is advantageous for distributing large sets of data into manageable smaller parts where the barrier for the verification of integrity is substantially reduced despite the overall larger data size. Even better, if we know where it is in the Merkle tree and we know the hashes of the branches we don't even need all of the transactions from