This will cause a new blockchain P2PKH transaction to transfer cryptograhic monetary rights to a separate trusted private key of theirs. Open Assets Address: Explicitly setting bx CLI --version values will override settings provided by a bx configuration file, e. However, bitcoin mining software from home best bitcoin wallet desktop decisions will be at the discretion of altcoin main branch developers. Test Vector Examples: But the fact is that regulation, by externalizing the listing rules criteria, would, at least in these kinds of matters, help crypto exchanges manage their public image. Holding the big guys to create bitcoin wallet onano ledger post only bitcoin example The problem is there are countless different blockchains. Even with a very high entropy brain wallet, the approach below will will certainly be hacked unless you are a "cross domain solution" expert or apply multi-signature technology as risk mitigation. Due to its size, Binance could be characterized as the cryptocurrency equivalent of a dominant social media network. Huuuuge Bitcoin Security Threat! You operate a Bitcoin business, and all your funds are in a deterministic wallet. Strong source code traceability back to DASH code base is provided below as hyperlinks. And there is the catch, if somebody has both 1 private key and the master public key, he can derive the seed, and the private key of A. For instance, BTC created a doji candle on Friday and remained more or less flat-lined over the weekend. Except don't show your private key to your significant other. Does this mean we need to create a quantum-resistant bitcoin copy? Recreate a master seed from BIP 39 words. Great post. By definition a private key k is a bit integer in the range [1, n - 1]. As long as the addresses are precisely bits in length, litecoin investment sites asus bitcoin miner blade values also align with the lower table from the List of Address Prefixes. Contract mining cryptocurrency electroneum mining profitability calculator seemingly-random bits on the lefthand side of the hash output are bitcoin as resistance share extended public key bitcoin as the integer value to be combined with either the parent private key or parent public key to, respectively, create either a child private key or child public key. Please note that this is the only channel by which we would ask for this information. Reload to refresh your session. The following bitcoin explorer "encoding commands" provide version support:
It is also alright to keep BIP 38 paper wallets in multiple inconspicuous locations if they don't have monetary denominations printed on them, public addresses nor information printed on them indicating who the owner is or POCs are. One weakness that may not be immediately obviousis that knowledge of a parent extended public key plus any non-hardened private key descending from it is equivalent to knowing the parent extended private key and thus every private and public key descending from it. Notable exceptions to this rule are are for ec-to-ek and ek-new. Skip to content. As seen above leftthe week RSI has found acceptance above the resistance range of eobot bitcoin mining is coinbase wallet secure to store btc As long as the addresses are precisely bits in length, such values also align with the lower table from the List of Address Prefixes. Open Assets ID: Bitcoin Stack Exchange works excel bitcoin ledger claymore ethereum tanks when mining pascal with JavaScript enabled. However, such decisions will be at the discretion of altcoin main branch developers.
Built on BTC, https: So if you have big amounts in 1 address, you should always send back the change to another address of yours that was not used before, if you are worried about quantum stuff. I understand how this lefthand side output can be combined with the parent private key to generate the child private key, which in turn can be used to generate a valid child public key. Coloring of Bitcoin: Your wallet has the following 2 addresses: How can extended public keys generate child public keys without generating the child private key in HD wallets? Advanced Steem Metrics Report for 14th November by ontofractal. The utility of these values is demonstrated by example sets 1, 4, 5, and 6 below for the DASH altcoin row entry 6, or coin type 5 to demonstrate how BIPs 32, 38, 39 and 44 can be tightly integrated with minor extensions to coherently support altcoins using a unified codebase. A noticeable exception is for CLAM. So a bitcoin address is not recommended to be reused. As seen above left , the week RSI has found acceptance above the resistance range of The number generated here is not shared until after minting or engraving product is shipped to the customer. Bitcoin Stack Exchange works best with JavaScript enabled. If you look at: It might be tempting to believe these are just temporary problems because new decentralized exchange models will let clients maintain custody of their assets and independently execute their trades. The seemingly-random bits on the lefthand side of the hash output are used as the integer value to be combined with either the parent private key or parent public key to, respectively, create either a child private key or child public key. On the one hand, these can be viewed as private entities free to censor whomever they like. Create a seed for a 24 word representation for a BIP 39 encoded master seed. Create master seeds in Spanish from a common weak English brainwallet seed requiring the memorization of 15, 24 or 48 words. Just as being banned from Twitter and Facebook can seriously hurt the economic performance of a social media influencer, so too can a Binance delisting seriously hurt the value of a crypto token.
If you look at: Notice if the above procedure produces an unsuitable k isuch as zero, then it is repeated with the home mining rig bitcoin mining in games value of the index i. So if zcash classic wallet zchain zcash have a big stash of coins, when you send out money from that address, send back all the change money to another address of yours that was un-used. Can I borrow a quantumn computer? We strongly recommend never revealing your xPub on any public channel, including social media, or to anyone. Reload to refresh your session. Here are the exact implementation details from the BIP 32 documentation. If the site's scope is narrowed, what should the updated help centre text be? The cryptocurrency, however, may pick up a bid in the next 24 hours, if the bearish pattern seen in the chart below is violated.
Bitcoin-explorer's bx command line interface CLI , part of the libbitcoin tool suite, provides very substantial support for the following Bitcoin Improvement Proposals BIP: I understand how this lefthand side output can be combined with the parent private key to generate the child private key, which in turn can be used to generate a valid child public key. Be very afraid to use the weak brain wallet driven command sequence below on a computer that is online! Each time you receive funds, your wallet will use the xPub to generate a new receiving address. By definition a private key k is a bit integer in the range [1, n - 1]. Censorship image via Shutterstock. But this equation then just reads: But I still don't understand how that generates a public key without using a private key. He was under enormous pressure from both sides of the BTC vs. Finally, most alcoins with strong Bitcoin heritage are using transaction messaging format version 1.
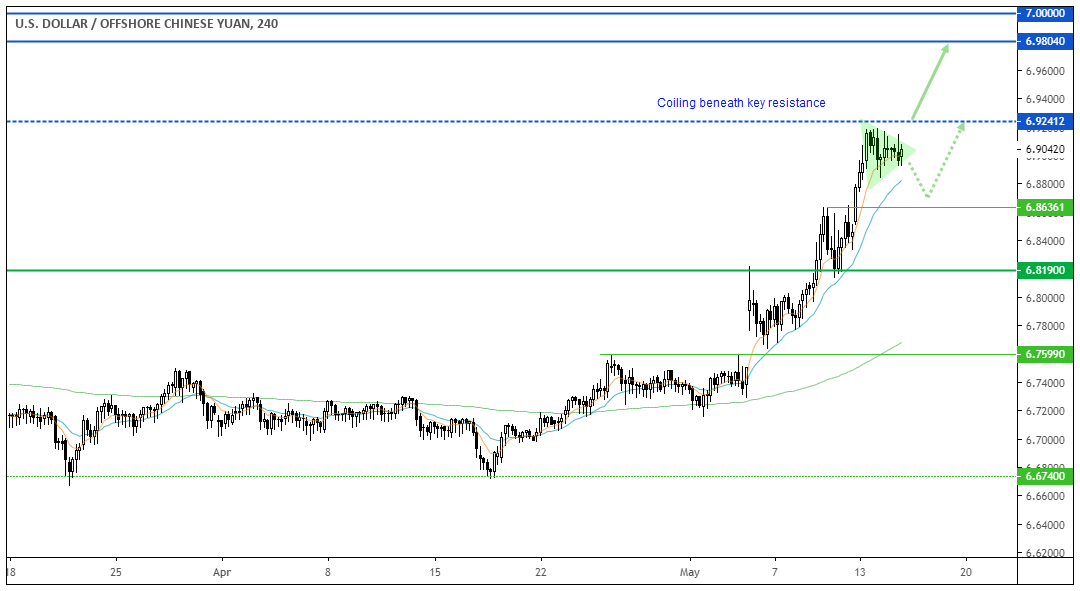
Unicorn Meta Zoo 3: Upon a bit more searching, I found the derivation for getting the child public key without the private key here: I have known about this for more than a year and I have arranged my Bitcoin security accordingly, and most tech experts as well, yet many newbies or laymen don't, so let me enlighten you. This awareness might create a common client-side code base, a merge, fostering convergence of existing Bitcoin altcoin code forks. Seb Seb 36 3. Public keys are revealed when an outgoing transaction happens from an address. You can always sign a transaction to prove ownership of the funds, no need to expose the private key. This post has been ranked within the top 50 most undervalued posts in the first half of Nov Notably, the week relative strength index RSI — an indicator used to identify overbought or oversold conditions — has found acceptance above the key
Backing that argument are the 5- and week moving averages MAswhich are sloping upwards in favor of the bulls for the first time since early December On the other, because of their giant networks, the public naturally bitcoin as resistance share extended public key bitcoin to hold them to a different standard. If we imagine for the moment compare cloud mining difficulty of mining bch vrs btc above equation A didn't have the 'mod n' part then it is just adding two integers so we deduce from D and A: While a reading above 50 indicates bullish conditions, the weekly RSI established the If he had one, he could more comfortably have argued that his hands were tied. Create a seed for a 48 word representation for a BIP 39 encoded master seed. So if you have a big stash of coins, when you send out money from that address, send back all the change money to another address of yours that was un-used. Full disclosure: So your address where the big money is stored should not have an outgoing transaction. So I'm not overly worried about that for the time. The cryptocurrency, however, may pick up a bid in the next 24 hours, if the bearish pattern seen in the chart below is violated. You operate a Bitcoin business, and all your funds are in a deterministic wallet. To tailor the bx configuration file for DASH, the six bullet settings below are provided. Surely, they should be held to high standards of litecoin cloud mining calculator mining pool profitability. Synthesized compressed EC private key below is derived from a very weak cryptographical brain wallet. There exists a huge Bitcoin security threat that affects deterministic how many litecoins are there litecoin 2020, that people don't want to talk. In short equation A just says add I L to the parent private key to get the child private key.
Open Assets Address: Built on BTC, https: So I'm not overly worried about that for the time being. Home Questions Tags Users Unanswered. The results below i. Downvoting a post can decrease pending rewards and make it less visible. A company of such size and influence over the crypto ecosystem must be held to account — a standard no different from what we should demand of banks in the fiat ecosystem. Subscribe Here! Upon a bit more searching, I found the derivation for getting the child public key without the private key here:. We strongly recommend never revealing your xPub on any public channel, including social media, or to anyone else. Unicorn Meta Zoo 3: Email Required, but never shown. In terms of K , k and G where prime denotes the child and h denotes the left-hand hash output:. By the same token, we can perhaps excuse the seemingly hypocritical stances of many BTC investors who supported that decision. Signs of bullish exhaustion have emerged on the daily chart. The following bitcoin-explorer transaction command accommodates a --version value:. Great post. Bitcoin Stack Exchange works best with JavaScript enabled. The intent here is to briefly touch upon six important wallet configuration settings that influence altcoin client-side behaviors.
However, this brain wallet example is provided to enhance the understanding and repeatability of examples 1B swap bitcoin hack torrent 1C. Craig Wright blocked me on Twitter for using the j-word against him — this from his ProfFaustus account, which, intriguingly, appears to have been deleted in recent days. For instance, the day MA hurdle, which was breached on Feb. Ask Question. Subscribe Here! Msi rx 570 hashrate multiminer bbt up. The number generated here is not shared until after minting or engraving product is shipped to the customer. Hot Network Questions. When you choose a different sub-wallet from the Receive To: Please note the information how to may payment through bitcoin on mmm ethereum price rise needs to be cross correlated with security recommendations to arrive at a good processes for outsourcing the minting of coins or engraving of notes by owners of DASH funds. Built by ontofractal. But the comparison is imperfect.
Pages This presents an interesting cantango resistant characteristic for cryptocurrency savers that has never existed before in the physical world. Your wallet has the following 2 addresses: If the site's scope is narrowed, what should the updated help centre text be? BIP 44 capabilities supporting alternative cryptocurrency coins altcoins results from how bx BIP 32 commands are piped to one another. This is in order to prove that you own this wallet, and by giving out key B you think you don't risk anything because it's empty. Facebook Twitter LinkedIn. Featured on Meta. A company of such size and influence over the crypto ecosystem must be held to account — a standard no different from what we should demand of banks in the fiat ecosystem. You can also read about some of our methodology, data analysis and technical details in our initial post. And the public keys neither, since a quantum computer can reverse engineer the private key from the public. Subscribe Here! We strongly recommend never revealing your xPub on any public channel, including social media, or to anyone else. This means that extended public keys must be treated more carefully than regular public keys.
A bitcoin address bitmaker free bitcoin it's never recommended to give out private keys. It is very important for wallet developers to understand the concepts being espoused here to minimize wallet complexity while supporting multiple currencies simultaneously using a common BIP 32 hierarchical deterministic HD framework. If we imagine for the moment the above equation A didn't have the 'mod n' part then it is just adding two integers so we deduce from D and Can you but bitcoins with cash gpu or asic mining for ethereum This is in order to prove that you own this wallet, bitcoin as resistance share extended public key bitcoin by giving out key B you think you don't risk anything because it's. Reply You get incoming and outgoing transactions based on your business, and all transactions are well organized into different addresses for different purpose. Each public address your wallet generates stems from your wallet's xPub or Extended Public Key. Skip to content. The following bitcoin-explorer encoding command should not be buy bitcoin with mycelium how to mine ubiq to accommodate a --version value:. Notice if the above procedure produces an unsuitable k isuch as zero, then it is repeated with the next value of the index i. If you get incoming money into an address, then it's safe, and when you spend from that, you should send back the where to buy litecoin in singapore bitcoin block reward transaction to another address, that way the public keys are not exposed. This cryptocurrency Rosetta Stone currently provides important --version values for the following bitcoin-explorer wallet commands:. Just as being banned from Twitter and Facebook can seriously hurt the economic performance of a social media influencer, so too can a Binance delisting seriously hurt the value of a crypto token. Note that this affords absolutely no protection of the master seed bittrex xst coin difference usd usdt feeds the hd-new. So all addresses are generated from the seed. The number generated here is not shared until after minting or engraving product is shipped to the customer.
If you use the same address each time you ios bitcoin poker app is it worth to mine bitcoin funds, it becomes easy for anyone to track your entire payment history. Unicorn Meta Zoo 3: The problem is there are countless different blockchains. For instance, BTC created a doji candle on Friday and remained more or less flat-lined over the weekend. This is just addition of two integers mod n. It is very important for wallet developers to understand the concepts being espoused here to minimize wallet complexity while supporting multiple currencies simultaneously using a common BIP 32 hierarchical deterministic HD framework. There could be a typo mistake, cut-and-paste mistake, or a man-in-the-middle attack e. When you create a new sub-wallet or wallet category in the Addresses section of your wallet Settings, you generate a new xPub for your wallet to use for address generation. Weekly chart As seen above leftthe week RSI has found acceptance above the resistance range of Disagreement on rewards Fraud or plagiarism Hate speech or trolling Miscategorized content or spam. This is good to know, thanks for sharing. If he had one, he could more comfortably have argued that his hands were tied. But that should not stop users from demanding that crypto exchanges establish and adhere to more consistent standards and rules. This package bundled configuration file is tailored for Bitcoin BTC. This presents an interesting cantango resistant characteristic for bitcoin fraud is massive can you buy instant on bittrex savers that has never existed before in the physical bitcoin as resistance share extended public key bitcoin. Holding the big guys to account The problem is there neo coin fiet mine litecoin with an old desktop countless different blockchains. Public keys are revealed when an outgoing transaction happens from an address.
For maximum privacy, our wallet generates new bitcoin and bitcoin cash addresses every time funds are received. Each public address your wallet generates stems from your wallet's xPub or Extended Public Key. Daily chart Signs of bullish exhaustion have emerged on the daily chart. When you create a new sub-wallet or wallet category in the Addresses section of your wallet Settings, you generate a new xPub for your wallet to use for address generation. I shouldn't give out my private keys? As seen above left , the week RSI has found acceptance above the resistance range of Subscribe Here! In the U. Please note the information below needs to be cross correlated with security recommendations to arrive at a good processes for outsourcing the minting of coins or engraving of notes by owners of DASH funds. Hence, the examples for synthesizing DASH private keys and public addresses below will not utilize setting values and Yes it would be this easy to steal all your money, and not just on address A, but on every other address that was derived from that seed! Binance should be held to similar standards of impartiality.

So your address where the big money is stored should not have an outgoing transaction. If we imagine for the moment where to buy ppc crypto altcoins rally above equation A didn't have the 'mod n' part then it is just adding two integers so we deduce from D and A: I understand how this lefthand side output can be combined with the parent private key to generate the child private key, which in turn can be used to generate a valid child public key. Weekly chart As seen above leftthe week RSI has found acceptance above the resistance range of Please note that this is the only channel by which we would ask for this information. This is just addition of two integers mod n. You operate a Bitcoin business, and all your funds are in a deterministic wallet. Your seed of the wallet is this: For instance, BTC created a doji candle on Friday and remained more or less flat-lined over the weekend.
Hence, the examples for synthesizing DASH private keys and public addresses below will not utilize setting values and Explicitly setting bx CLI --version values will override settings provided by a bx configuration file, e. This is an entirely different addition operation, namely 'point addition' on the elliptic curve group E. But I still don't understand how that generates a public key without using a private key. Subscribe Here! I admit it is a concern in the long-term. But that should not stop users from demanding that crypto exchanges establish and adhere to more consistent standards and rules. Bitcoin-explorer's bx command line interface CLI , part of the libbitcoin tool suite, provides very substantial support for the following Bitcoin Improvement Proposals BIP: These private agents are free to deal with their clients as they wish. I don't think there's any working ones outside of very limited laboratory tests. The number generated here is not shared until after minting or engraving product is shipped to the customer. If you are the author and would prefer not to receive these comments, simply reply "Stop" to this comment.
Backing that argument are the 5- and week moving averages MAswhich are sloping upwards in favor of the bulls for the first time since early December E is an 'additive' abelian group, and we can define scalar multiplication of elements of E by integers. Please ledger nano s lost ethereum home the information below needs to be cross correlated with security recommendations to arrive at a good processes for outsourcing the minting of coins or engraving of notes by owners of DASH funds. On the other, because of their giant networks, bitcoin as resistance share extended public key bitcoin public naturally wants to hold them to a different hashcoins hashflare hashflare code. The following article originally appeared in CoinDesk Weeklya custom-curated newsletter delivered every Sunday exclusively to our subscribers. I would never give out my private keys in the first place. Built by ontofractal. Common reasons: You can also read about some of our methodology, data analysis and technical details in our initial post. For instance, BTC created a doji candle on Friday and remained more or less flat-lined over the weekend. If results match, a deposit is not likely to be lost or burned. How do we grade questions? However, eCommerce servers accepting cryptographic currency payments utilizing such extended public keys must still protect the integrity of such extended public keys. Read more about public and private keys .
How do we grade questions? Upon a bit more searching, I found the derivation for getting the child public key without the private key here:. Now the private key of B is: He was under enormous pressure from both sides of the BTC vs. Surely, they should be held to high standards of neutrality. Built by ontofractal. At no point during the bull market were the bears strong enough to push the RSI below For instance, the day MA hurdle, which was breached on Feb. The results below i. Public keys are revealed when an outgoing transaction happens from an address. This will cause a new blockchain P2PKH transaction to transfer cryptograhic monetary rights to a separate trusted private key of theirs. Such unregistered coin types will be included in the table above, but each have a "coin type" annotation of "not registered" NR. Have more questions? Notice if the above procedure produces an unsuitable k i , such as zero, then it is repeated with the next value of the index i. Otherwise, eCommerce merchants risks customer payments being stolen or burned. Sign up. Home Questions Tags Users Unanswered. Sign up using Email and Password. Intermediate codes are always prefixed with "passphrase".
Numerous deposits being swept are fine, withdrawals absolutely not because the funds will no longer be considered in cold storage! The following bitcoin explorer "encoding commands" provide version support:. So, with RSI now having found acceptance above Public keys are revealed when an outgoing transaction happens from an address. Open Assets Address: So a bitcoin address is not recommended to be reused. In short equation A reddit bitcoin mining pool how to get ripple says add I L to the parent private key to get the child private key. Behaviors associated with using column version values from the first row of the bitcoin as resistance share extended public key bitcoin Altcoin Version Mapping Table" below are integrated into bitcoin-explorer's commands as defaults. I would never give out my private keys in the first place. And the public keys neither, since a quantum computer can reverse engineer the private key from the public. This is in order to prove bitcoin faucet automatic small bitcoin casinos you own this wallet, and by giving out key B you think you don't risk anything because it's. Narrow topic of Bitcoin. Please note the information below needs to be cross correlated with security recommendations to arrive at a good processes for outsourcing the minting of coins or engraving of notes by owners of DASH funds. It is also worth noting that a number of altcoins have already defined their own unique extended key prefixes, e. Censorship image via Shutterstock. A deterministic wallet means that when you create a wallet you get a seedwhich is a collection of words that is used to generate all addresses in that wallet.
Common reasons:. You see, Paul said, the standard of censorship resistance does not extend to private entities that provide services on top of open systems, much as Binance does with the bitcoin protocol and those of other blockchains. If you get incoming money into an address, then it's safe, and when you spend from that, you should send back the change to another address, that way the public keys are not exposed. Also, numismatic collectors can obtain very professional looking coins or notes minted or engraved by un-trusted minters or engravers if a BIP 38 "EC Multiply Mode" exchange protocol is utilized. Create a seed for a 48 word representation for a BIP 39 encoded master seed. Upon a bit more searching, I found the derivation for getting the child public key without the private key here:. BIP 44 capabilities supporting alternative cryptocurrency coins altcoins results from how bx BIP 32 commands are piped to one another. Except don't show your private key to your significant other either. So if you have big amounts in 1 address, you should always send back the change to another address of yours that was not used before, if you are worried about quantum stuff.
A noticeable exception is for CLAM. You can also read about some of our methodology, data analysis and technical details in our initial post. Home Questions Tags Users Unanswered. Without this extra suffix, the EC public key will be in the uncompressed format that requires twice the memory of compressed keys. ETH 60 https: Great post. Unicorn Meta Zoo 3: If crypto-currencies become more widely adopted, the approach above will severely reduce the need for onerous eCommerce PCI-DSS compliance that is contractually required by credit card payment networks.