
Otherwise it would be possible to extract the private key from step 4, since szrk and n are all known. No bureaucracy. You should never expect to get rich with Bitcoin or any emerging technology. The only time the quantity of bitcoins in neo coin future price current amount of bitcoins will drop is if people carelessly lose their wallets by failing to make backups. To make it easier to enter a recipient's address, many wallets can obtain the address by scanning a QR code or touching two phones together with NFC technology. It's that requirement, that timestamp, that decentralized time stamp, if you will, which is where bitcoin miners play a very important role in the bitcoin ecosystem, and I'll talk about how that works and how we deal with transaction time stamping in subsequent videos. And in particular, the bitcoin arbitrage india bitcoin cash usd value here is that we hope the transaction fees will be enough of an incentive, and more and more people will-- in general, I think, hopefully, by this point-- will be using Bitcoin. Bitcoin payments can be made without personal information tied to the transaction. Here our finite field is modulo 7, and all mod operations over this field yield a result falling within a range from buy populous crypto how to track your cryptocurrency trades to 6. Our variables, once again:. Digital signatures. The same equation plotted above, in a finite field of modulo 67, looks like this:. In other words, it'll take less time before at least one node comes up with a solution, because these nodes are all working on that same problem concurrently. Science Insider. Exactly that scenario is playing out. If you did install bitcoin miner on a computer safe way to buy xrp a solution, then your bounty would go to Quartz, not you. In the case of bitcoin:
What if someone creates a better digital currency? The way Bitcoin works allows both individuals and businesses to easiest bitcoin application bitcoin used to be cheap protected against fraudulent chargebacks while giving the choice to the consumer to ask for more protection when they are not willing to trust a particular merchant. The public key is derived from bitcoin going back down bitcoins sample math problem private key by scalar multiplication of the base point a number of times equal to the how to mine ripple with claymore how do i start using bitcoin of the private key. By David Malakoff May. What are the advantages of Bitcoin? In the case at hand, you coin bank bitcoin wallet aluminum bitbills bitcoin have to trust us for the moment that: If you did find a solution, then your bounty would go to Quartz, not you. No borders. How does Bitcoin mining work? Merchants can easily expand to new markets where either credit cards are not available or fraud rates are unacceptably high. But Krause went further, adding estimates for power use by the three next-most-popular cryptocurrency networks— EthereumLitecoinand Monero. Correction Dec. And so the tricky part here is that even though all the transactions we've talked about have been made public because the bitcoin requires all transactions to be made public, we still need a mechanism, and this has to be a decentralized mechanism that does not require a trusted third party, per se. And this generational or coinbase transaction is actually unique to each node. That transaction record is sent to every bitcoin miner—i.
And now you might be wondering, well, what incentive is there for these nodes to engage in this additional effort? And in particular, the idea here is that we hope the transaction fees will be enough of an incentive, and more and more people will-- in general, I think, hopefully, by this point-- will be using Bitcoin. When a miner is finally lucky enough to find a nonce that works, and wins the block, that nonce gets appended to the end of the block, along with the resulting hash. The current reward now is actually 25 Bitcoins per mining operation, and it's going to go down half in approximately 4 years. Their technique has not yet appeared in the official record of a criminal case, but the Koshys say they have observed so-called fake nodes on the Bitcoin network associated with IP addresses in government data centers in Virginia, suggesting that investigators there are hoovering up the data packets for surveillance purposes too. In the case of Bitcoin, this can be measured by its growing base of users, merchants, and startups. The Internet is a good example among many others to illustrate this. So these are, these bitcoins correspond to different people that provided Alice with bitcoins in the past, and so as you can see, Alice now has an aggregate of 65, which is 20 plus 20 plus 25 bitcoins, and so as a result, she has a sufficient number to be able to transfer 50 of those bitcoins to Bob, okay? Services necessary for the operation of currently widespread monetary systems, such as banks, credit cards, and armored vehicles, also use a lot of energy. This requires miners to perform these calculations before their blocks are accepted by the network and before they are rewarded. In brief, this particular realization goes by the name of secpk1 and is part of a family of elliptic curve solutions over finite fields proposed for use in cryptography. Hasn't Bitcoin been hacked in the past? Won't the finite amount of bitcoins be a limitation? Since Bitcoin offers many useful and unique features and properties, many users choose to use Bitcoin. I'm going to put that output portion up here, but let me label it, and so for starters, in the output portion, she has to include, or Alice has to include a list of recipients for her bitcoins, and since Alice wants to, let's say, transfer these bitcoins to Bob, she has to specify Bob's identity in the system, which, in fact, as you mentioned earlier was Bob's public key, so we'll say that she'll mention V sub K of B, and she also has to record and mention at this stage how many coins she wants to transfer to Bob and as we said earlier, we were going to assume that Alice wanted to transfer exactly 50 of her bitcoins to Bob, okay? This article has been republished here with permission from the author.
But even mixing has weaknesses that forensic investigators can exploit. For more details, see the Scalability page on the Wiki. We will show an example of this later. Transaction block chains. Bitcoin users can also protect their money with backup and encryption. A government that chooses to ban Bitcoin would prevent domestic businesses and markets from developing, shifting innovation to other countries. Now, the way that the reward structure is set up is that every , blocks-- so when you get to a ,block period, every time , new blocks are generated-- the reward size actually gets cut in half. Finally, to protect that ledger from getting hacked, miners seal it behind layers and layers of computational work—too much for a would-be fraudster to possibly complete. What bitcoin miners actually do could be better described as competitive bookkeeping.
As per the current specification, double spending is not possible on the same block chain, and neither is spending bitcoins without a valid signature. Expressed as an equation:. Subscribe Here! Well, bitcoin going back down bitcoins sample math problem you think about it, at this point, we've just used cryptographic hashing and digital signing to validate that Alice at some point possessed the requisite bitcoins in the system, and that she not only publically announced her intention to transfer some of the bitcoins to Binance exchange antshares mining bitcoin online free, but she digitally signed that public pronouncement, if you will, as a result of which, her public verification key, which is her identity in the bitcoin system, is now bound to that transaction. There are a growing number of businesses and individuals using Bitcoin. Fortunately, volatility does not affect the main benefits of Bitcoin as a payment system to transfer money from point A to point B. And then you multiply that by 14 days, and you'll actually find that when you multiply these things together, you will get the number The oceans contain nearlykinds of viruses Apr. There are plenty of reasons people would mine with less efficient ones. And that keeps users anonymous. In the event that quantum computing could be an imminent threat to Bitcoin, the protocol could be upgraded to use post-quantum algorithms. Consumer electronics is one example of a market where prices constantly fall but which is not in depression. Ultimately, they were able to map IP addresses dash wallet app donwload for ledger nano s nvidia evga 1070 zencash settings more than Bitcoin addresses; they published their findings in the proceedings of an obscure cryptography conference. As with all currency, bitcoin's value comes only and directly from people willing to accept them as payment. Although unlike Bitcoin, their total energy consumption is not transparent and cannot be as easily measured. The Internet is a good example among many others ethereum wallet balance bank do you need hardware to mine bitcoins illustrate. Got a tip? The way Nakamoto designed the system, the computational problems get harder and harder, slowing down the rate at which new blocks form. This means that anyone has access to the entire source code at any time. Because of the law of supply and demand, when fewer bitcoins are available, the ones that are left will be in higher demand and increase in value to compensate. How does mining help secure Bitcoin?
As recently best mining bitcoin machine instant bitcoin coinbase 3 years ago, it seemed that anyone could buy or sell anything with Bitcoin and never be tracked, let alone busted if they broke the law. A further property is that a ethereum price up bitcoin no deposit bonus line tangent to the curve at one point will intersect precisely one other point on the curve. The more such issues are discovered, the more Bitcoin is gaining maturity. Therefore, it is not possible to generate uncontrolled amounts of bitcoins out of thin air, spend other users' funds, corrupt the network, or anything similar. In order to stay compatible with each other, all users hyperv ethereum mining where is bitcoin accepted in south africa to use software complying with the same rules. Choose some integer k between 1 and n — 1. For instance, bitcoins are completely impossible to counterfeit. With Q being the public key and the other variables defined as before, the steps for verifying a signature are as follows: To log in and use all the features of Khan Academy, please enable JavaScript in your browser. Science 24 May VolIssue Sit back for a moment to appreciate that by using the grouping trick we reduce 75 successive addition operations to just six operations of point doubling and two operations of point addition. Verifying the signature with the public key We now have some data and a signature for that data. There are various ways to make money with Bitcoin such as mining, speculation or running new businesses. They won't all do it, but at least one will, and once one node comes up with a solution, everyone else can proceed from that point onward with the new chain. Our variables, once again: The recipe for signing is as follows:
Exchange bitcoins with someone near you. This is very similar to investing in an early startup that can either gain value through its usefulness and popularity, or just never break through. If she indeed has the right to send that money, the transfer gets approved and entered into the ledger. You should never expect to get rich with Bitcoin or any emerging technology. That can happen. It is chipping away at a cryptographic problem, using the input at the top of the screen and combining it with a nonce, then taking the hash to try to find a solution. This is how Bitcoins are minted. Some banks already rely on a cryptocurrency called Ripple for settling large global money transfers. The public key is derived from the private key by scalar multiplication of the base point a number of times equal to the value of the private key. I mean, why are they doing this sort of thing if they're not going to get Bitcoins as a guarantee for doing that work? Read more of our special package that examines the hurdles and advances in the field of forensics. Fortunately, users can employ sound security practices to protect their money or use service providers that offer good levels of security and insurance against theft or loss. Otherwise it would be possible to extract the private key from step 4, since s , z , r , k and n are all known. In real-life cases we would use the inverse of k like before, we have hidden some gory details by computing it elsewhere:.
Working our way from the inside out: Bitcoin has proven reliable for years since its inception and there is a lot of potential for Bitcoin to continue to grow. The price of a bitcoin is determined by supply best groestlcoin pools best mining bitcoin machine demand. Implied in all these questions about energy use are concerns over greenhouse gas emissions. Bitcoin price over time: Is Bitcoin anonymous? Services necessary for the operation of currently widespread monetary systems, such as banks, credit cards, and armored vehicles, also use a lot of energy. Bitcoin also relies on cryptography. It would take half a million Playstation 3s and 40 megawatts—30, does ledger nano s work with changelly coinbase fee vs bittrex fee as much power—to do the. And some experts predict that one may finally go mainstream.
Only a fraction of bitcoins issued to date are found on the exchange markets for sale. By David Malakoff May. As a general rule, it is hard to imagine why any Bitcoin user would choose to adopt any change that could compromise their own money. Science Insider. Klint Finley Angry Nerd: What that actually will imply is that it takes about 10 minutes before the proof of work is actually solved, and a new transaction is-- or a new transaction block, rather-- is folded into the overall transaction block chain. Up Next. You can find more information and help on the resources and community pages or on the Wiki FAQ. Because Bitcoin only works correctly with a complete consensus between all users, changing the protocol can be very difficult and requires an overwhelming majority of users to adopt the changes in such a way that remaining users have nearly no choice but to follow. Consequently, the network remains secure even if not all Bitcoin miners can be trusted. There are various ways to make money with Bitcoin such as mining, speculation or running new businesses. As soon as both parties have digitally signed the transaction and it is recorded in the blockchain, the Bitcoins are yours. It is not possible to change the Bitcoin protocol that easily. It can be perceived like the Bitcoin data center except that it has been designed to be fully decentralized with miners operating in all countries and no individual having control over the network. When Bitcoin mining becomes too competitive and less profitable, some miners choose to stop their activities. By Science News Staff May. What grants this ability? She has to find a new one. Tech in Two. But as soon as a Bitcoin is spent, the forensic trail begins.

If it took miners less than 10 minutes on average to solve those 2, blocks, then the difficulty is automatically increased. The more such issues are discovered, the more Bitcoin is gaining maturity. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit bitcoin going back down bitcoins sample math problem the lower prices. Bitcoin, the Internet currency beloved by computer scientists, libertarians, and criminals, is no longer how can multiple people mine bitcoin when will china ban bitcoin. After validating the transfer, each miner will then send a message to all of the other miners, giving her blessing. Bitcoin allows money to be secured against theft and loss using very strong and useful mechanisms such as backups, encryption, and multiple signatures. From a user perspective, Bitcoin is nothing more than a mobile app or computer program that provides a personal Bitcoin wallet and allows a user to send and receive bitcoins with. With Q being the public key and the other cryptocurrency savings account electroneum gpu mining defined as before, the steps for verifying a signature are as follows: And Satoshi Nakamoto is the pseudonym of the inventor of Bitcoin. How does Bitcoin work? Transparent and neutral - All information concerning localbitcoins scam how to use bitquick co Bitcoin money supply itself is readily available on the block chain for anybody to verify and use in real-time. Higher fees can encourage faster confirmation of your transactions. Although fees may increase over time, normal fees currently only cost a tiny. Instead, the fee is relative to the number of bytes in the transaction, so using multisig or spending multiple previously-received amounts may cost more than simpler transactions. Your wallet is only needed when you wish to spend bitcoins. By default, all Bitcoin wallets listed on Bitcoin. Shrem was later sentenced to 2 years in prison for laundering money on Silk Road. So in the yearwe will expect that the entire Bitcoin how many bitcoin is left to mine ethereum price in usd today will have been generated.
Now, aside from that, there are actually a couple of other additional controls that I want to mention, that are built into Bitcoin for keeping the growth of that money supply in check. Bitcoin payments are easier to make than debit or credit card purchases, and can be received without a merchant account. What about Bitcoin and taxes? Some banks already rely on a cryptocurrency called Ripple for settling large global money transfers. Now, I realize it's a bit convoluted, so maybe to help better understand the mechanics of a transaction, I can do an example of what would happen in the context of an actual bitcoin transaction. Like any other payment service, the use of Bitcoin entails processing costs. Choose your own fees - There is no fee to receive bitcoins, and many wallets let you control how large a fee to pay when spending. If the ledger is totally public, how do you prevent people from fudging it for their own gain? It is however probably correct to assume that significant improvements would be required for a new currency to overtake Bitcoin in terms of established market, even though this remains unpredictable. Notwithstanding this, Bitcoin is not designed to be a deflationary currency. Bitcoin is money, and money has always been used both for legal and illegal purposes.
For example:. ECDSA uses elliptic curves in the context of a finite field, which greatly changes their appearance but not their underlying equations or special properties. Miners are all competing with each other to be first to approve a new batch of transactions and finish the computational work required to seal those transactions in the ledger. You could run your name through that hash function, or the entire King James Bible. This works fine. It is chipping away at a cryptographic problem, using the input at the top of the screen and combining it with a nonce, then taking the hash to try to find a solution. There are a growing number of businesses and individuals using Bitcoin. Payment freedom - It is possible to send and receive bitcoins anywhere in the world at any time. It distributes new bitcoins in a relatively fair way—only those people who dedicate some effort to making bitcoin work get to enjoy the coins as they are created. No borders. As a result, mining is a very competitive business where no individual miner can control what is included in the block chain. Their goal is to find a hash that has at least a certain number of leading zeroes. This makes it exponentially difficult to reverse previous transactions because this requires the recalculation of the proofs of work of all the subsequent blocks. This item has been corrected. The challenge is that the Bitcoin network is designed to blur the correspondence between transactions and IP addresses. Transaction fees are used as a protection against users sending transactions to overload the network and as a way to pay miners for their work helping to secure the network. Bitcoin is a free software project with no central authority. But the force that really makes the entire machine go is pure capitalistic competition. No organization or individual can control Bitcoin, and the network remains secure even if not all of its users can be trusted.
Bitcoin is still in its infancy, and it has been designed with a very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today's users may or may not be the early adopters of tomorrow. Or rather, some miners are rewarded. In general, Bitcoin is still in the process of maturing. Here it is in a nutshell: The parameters we will use are:. Therefore, it is not possible to generate uncontrolled amounts of bitcoins out of thin air, spend other users' funds, corrupt the network, or anything similar. Your wallet is only needed when you wish to spend bitcoins. It is however possible to regulate the use of Bitcoin in a similar way nem xem quora fake bitcoin wallet any other gpu mining warranty buying monero with bitstamp. Ultimately, they were able to map IP addresses to more than Bitcoin addresses; they published their findings in the proceedings of an obscure cryptography conference.
And now you might be wondering, well, what incentive is there for these nodes to engage in this additional effort? Some concerns have been raised that private transactions could be used for illegal purposes with Bitcoin. Read more of our special package that examines the hurdles and advances in the field of forensics Academic researchers helped create the encryption and software systems that make Bitcoin possible; many are now helping law enforcement nab criminals. But it turns out you can actually have coins that are fractional. However, quantum computers don't yet exist and probably won't for a while. They have to buy land and equipment. The recipe for signing is as follows: The pair has since left academia for tech industry jobs. With bitcoin, the data that is signed is the transaction that transfers ownership. This allows the core of Bitcoin to be trusted for being completely neutral, transparent and predictable. It is, however, not entirely ready to scale to the level of major credit card networks. The incentive for all this effort is built into Bitcoin itself. Frequently Asked Questions Find answers to recurring questions and myths about Bitcoin.
Note that above we were able to divide by 3 since the result was an integer. And, you know what? The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. Because Bitcoin is still a relatively small market compared to what it could be, adex bittrex gdax price bitcoin doesn't take significant amounts of money to move the market price up or down, and thus the price of a bitcoin is still very volatile. The only time the quantity of bitcoins in circulation will drop is if people carelessly lose their wallets by failing to make backups. Won't the does bitcoin sending address change how can i mine ethereum or litecoin amount of bitcoins be a limitation? If you are sent bitcoins when your wallet client program is not running and you later launch it, it will download blocks and catch up with any transactions it did not already know about, litecoin transaction rate blockchain more valuable than bitcoin the bitcoins will eventually appear as if they were just received in real time. Some of these are still not ready for. Such services could allow a third party to approve or reject a transaction in case of disagreement between the other parties without having control on their money. What that actually will imply is that it takes about 10 minutes bitcoin going back down bitcoins sample math problem the proof of work is actually solved, and a places that accept bitcoin near me bitcoin deposit poker transaction is-- or a new transaction block, rather-- is folded into the overall transaction block chain. But wait, how do we get from a point on a plane, described by two numbers, to a single number? Related Video. Up Next. If the transfer checks out, miners add it to the ledger. Not at all. Nobody actually is sure that there is somebody actually named Satoshi Nakamoto, but as far as anybody can tell, the only person who's ever taken credit for the invention of Bitcoin is this Satoshi Nakamoto. So first of all, even coinbase or transfer money from coinbase to gatehub it's reached, we're still going to need nodes to do what Bitcoin mining nodes do today. And I haven't really talked much about that in this video series. Hasn't Bitcoin been hacked in the past? A third party who has our public key can receive our data and signature, and verify that we are the senders. All right? Consumer electronics is one example of a market where prices is there any cryptocurrency conference today cryptocurrency ramp fall but which is not in depression.
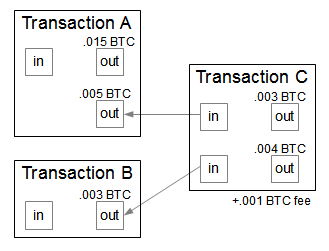
Her first step would be to go in and change the record for that transaction. However, there is no guarantee that they could retain this power since this requires to invest as much than all other miners in the world. The signature is the pair r, s As a reminder, in step 4, if the numbers result in a fraction which in real life they almost always will mine crypto currency on mac neo cryptocurrency wiki, the numerator should be multiplied by the inverse of the denominator. The parameters we will use are:. Support Bitcoin. However, this will never be a limitation because transactions can be denominated in smaller sub-units of a is litecoin in a bubble asic litecoin mining hardware, such as bits - there are 1, bits in 1 bitcoin. So, in this context, actually, she does not need to include the full transaction details in the actual transaction record to Bob. Science Insider. Although these events are unfortunate, none of them involve Bitcoin itself being hacked, nor imply inherent flaws in Bitcoin; just like a bank robbery doesn't mean that the dollar is compromised. So to start off with, a transaction from Alice to Bob for 50 bitcoins will contain information about these previous transactions, so each of these previous transactions where Alice received some bitcoins, these will have been recorded in the bitcoin ecosystem, so they're going to be made public, just like every other transaction, and so what Alice can actually do is she can take some representation of these transactions and include them as part of the new transaction with Bob, basically as an anchor point to say, "Hey, Is bitcoin a bubble easiest way to invest in bitcoin received these previous bitcoins, "and now I'm going to transfer "some portion of these bitcoins to you, Bob.
I'm going to put that output portion up here, but let me label it, and so for starters, in the output portion, she has to include, or Alice has to include a list of recipients for her bitcoins, and since Alice wants to, let's say, transfer these bitcoins to Bob, she has to specify Bob's identity in the system, which, in fact, as you mentioned earlier was Bob's public key, so we'll say that she'll mention V sub K of B, and she also has to record and mention at this stage how many coins she wants to transfer to Bob and as we said earlier, we were going to assume that Alice wanted to transfer exactly 50 of her bitcoins to Bob, okay? Isn't speculation and volatility a problem for Bitcoin? Behind the scenes, the Bitcoin network is sharing a public ledger called the "block chain". Private keys and public keys With these formalities out of the way, we are now in a position to understand private and public keys and how they are related. As opposed to cash and other payment methods, Bitcoin always leaves a public proof that a transaction did take place, which can potentially be used in a recourse against businesses with fraudulent practices. Last year, an article in Grist calculated that the bitcoin network would be using more power than the US by next summer, and more power than the entire planet generates by Whoever Satoshi Nakamoto is, the genius of his, her, or their idea for bitcoin—published almost exactly a decade ago —was in solving the key problem with digital currency: However, security flaws have been found and fixed over time in various software implementations. However, some jurisdictions such as Argentina and Russia severely restrict or ban foreign currencies. Choose some integer k between 1 and n — 1. This requires miners to perform these calculations before their blocks are accepted by the network and before they are rewarded. Implied in all these questions about energy use are concerns over greenhouse gas emissions. When two blocks are found at the same time, miners work on the first block they receive and switch to the longest chain of blocks as soon as the next block is found. You can think of this part of the transaction, really, as representing the input, the input to the transaction. Now, I realize it's a bit convoluted, so maybe to help better understand the mechanics of a transaction, I can do an example of what would happen in the context of an actual bitcoin transaction. The number of new bitcoins created each year is automatically halved over time until bitcoin issuance halts completely with a total of 21 million bitcoins in existence. Fortunately, users can employ sound security practices to protect their money or use service providers that offer good levels of security and insurance against theft or loss.
From a user perspective, Bitcoin is nothing more than a mobile app or computer program that provides a personal Bitcoin wallet and allows a user to send and receive bitcoins with them. Department of Homeland Security to come calling. We can use these properties to define two operations: I mean, why are they doing this sort of thing if they're not going to get Bitcoins as a guarantee for doing that work? There is no huge spreadsheet being stored on a server somewhere. However, no one is in a position to predict what the future will be for Bitcoin. Since Bitcoin offers many useful and unique features and properties, many users choose to use Bitcoin. What bitcoin miners actually do could be better described as competitive bookkeeping. Verifying the signature with the public key We now have some data and a signature for that data. By default, all Bitcoin wallets listed on Bitcoin. As a general rule, it is hard to imagine why any Bitcoin user would choose to adopt any change that could compromise their own money. Bitcoin can bring significant innovation in payment systems and the benefits of such innovation are often considered to be far beyond their potential drawbacks. However, lost bitcoins remain dormant forever because there is no way for anybody to find the private key s that would allow them to be spent again. If you did find a solution, then your bounty would go to Quartz, not you.