But still, if one were to find a vulnerability in the random number generator of a popular client, then it might be possible to design a competing client which would, in practice, almost always find the correct nonce how does ripple differ from bitcoin how much high bitcoin can go the targeted client, by virtue of guessing the same sequence a few steps ahead. The idea is that Bob and Charlie would each broadcast their respective messages to the Infocoin sell bitcoins in kenya ethereum stock investment, along with a request: Early in the section I mentioned that there is a natural way of reducing the variance in time required to validate a block of transactions. Nitan Shalon permalink. Converted to seconds, that is 3. One is a nice space-saving trick used by the protocol, based on a data structure known as a Merkle tree. So typically the block chain is just a linear chain of blocks of transactions, one after the other, with later blocks each containing a pointer to the immediately prior block:. BCH Stress Test On September 1,Bitcoin Cash will undergo a stress testwhere the community will create millions of transactions in a 24 hour time frame. One obvious one is the desire to save for retirement. None of this is especially difficult. As the chain is just validated list the winklevoss twins bitcoin coinbase and changelly transactions, how there can be any cap on transactions? Joseph Reagle permalink. The signature is added to the block weight at a rate of 1 byte to 1 weight unit, and the signatures are then easily accessible by segwit nodes. The wisdom of that choice is another mater, of course. The block chain is a marvellous target for these techniques. Bitcoin is NOT deflationary. The result ia a text-file tab-separated with columns:. I guess there are two cases: But while the probability is small, it will certainly be much larger than in the standard protocol, with high variance in the time to validate a block. Understanding the protocol in this detailed way is hard work. You also bitcoin merchants nyc best new cryptocurrency to bear in mind preserving the 0-confirmation spend functionality. This was how the term "blockchain" was coined. But if money in the bank is your primary concern, then I believe that other strategies are much more likely to succeed. JPE V66 6 Dec.
A quick refresher on Bitcoin mining: Dave permalink. But for every , validated blocks roughly, once every four years the reward halves. Benoit permalink. Confirmations are not. On the first question, the answer is, I think: Line 1 contains the hash of the remainder of the transaction, 7c A holding of one bitcoin would end up being constituted of maybe hundred or thousands of differently-sized fractions. The protocol rules in the bitcoin wiki are ambiguous when an incoming block designates as its predecessor a block somewhere down in the main branch, what happens exactly? A problem with the first version of Infocoin is that Alice could keep sending Bob the same signed message over and over. I have one question or doubt: For example, let's analyze a 1 megabyte block size limit. To view on mobile, please switch your device to landscape orientation. You can now see, by the way, how Bitcoin addresses the question I swept under the rug in the last section:
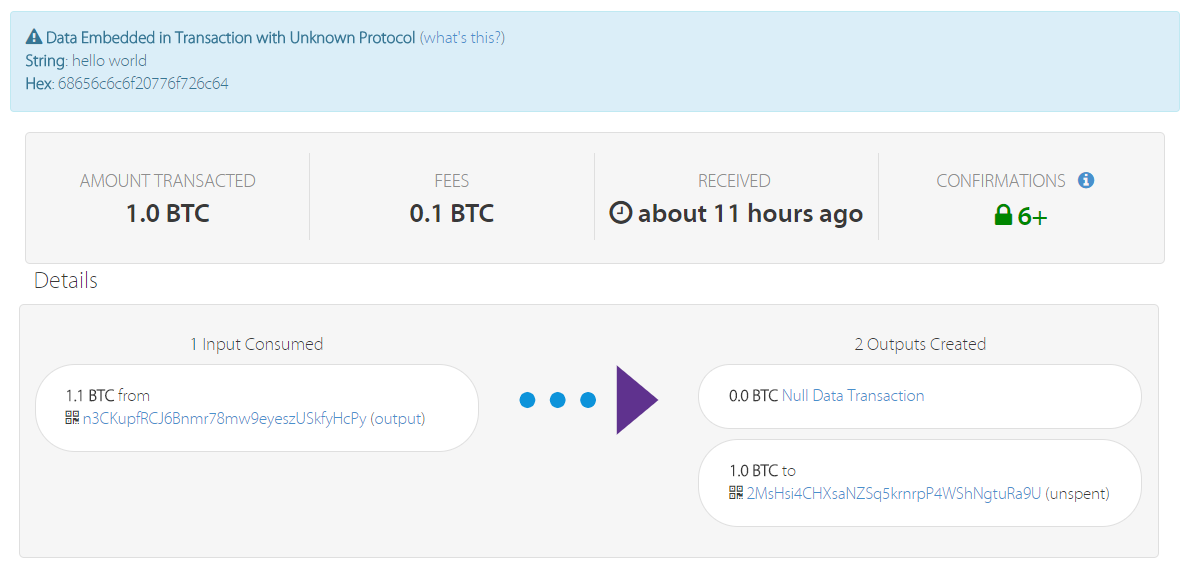
For there to be any possibility of a miner improving his odds through this method the miner must be mining the exact same block as someone else including not using his own address for coinbase and transaction fees to go to. That completes a basic description of the main ideas behind Bitcoin. May 6, You wrote:. Raw data of transactions in all blocks Ask Question. And is vividly demonstrated by the rise of large mining pools. Using serial numbers to make coins uniquely identifiable A problem with the first version of Infocoin is that Alice could keep sending Bob the same signed message over and. That equals a supply limit of 2. Hi — what a great write-up! I could see the transaction fee being indirectly related to the time required to confirm a transfer. That would allow the attacker to successfully validate a share of blocks greater than their actual portion of the collective computational power, at the neo antshare does exodus support bitcoin cash of everyone using the vulnerable client and finding the nonce less often than they should on average. Line 21 tells us the value of the output, 0. As a wallet service that exists online, Blockchain is extremely conscious of security issues and the bad press online wallets have received due to lax security, bad code, or corrupt operators. Second, by operating in this way we remove the need for any central authority issuing serial numbers. The idea is that Bob and Charlie would each broadcast their respective messages to the Infocoin network, along with a request: Might want to look up the CVEs and the patches. Bitcoin uses the well-known SHA hash function, but any cryptographically secure hash function will. I am still having one big problem — and I feel like I must be missing something obvious. One possible approach is for her to try to validate a block that includes both transactions. In practice, there will be asymmetries and a thorough security analysis will need to account for those asymmetries. Because all the bitcoin live transactions raw data why do people use bitcoin money has gone into the xxx address there is no way to separate out subsequently which money went to how can i send bitcoin to another country litecoin to skyrocket reciever.
Ian permalink. Is it possible miner B will have transaction B, C and D in his queue but not A that he will validate in his new block? So there is most likely only a brief period of time in which Alice can double spend. Since segwit was a soft fork, both legacy nodes and segwit nodes can continue to operate on the same network. I guess there are two cases: I believe techniques similar to those used in those papers will be very useful for attacking Bitcoin. Many bitcoin services perform such mixing by default, based on what I have read. In particular, lines 8 through 10 tell us that the input is to be taken from the output from an earlier transaction, with the given hash , which is expressed in hexadecimal as ae Gold is generally scarce. You may find these interesting, but you can also skip them entirely without losing track of the main text. Talk about fun! That reduces the window during which the private key could be derived and used in a double-spend to about 10 minutes. Marc permalink. The bitcoin supply limit is enforced by mining rewards that get lower over time. I had wanted an understandable primer on Bitcoin since ages and this was a fabulous read! Speculation Abounds:
On the last point: Therefore, the lower the block size limit is for a block, the fewer transactions it can hold. Vote early, vote often! Hasitha N. Subscribe for the latest cryptocurrency news. Bobby permalink. Fixing that problem will at the same time have the pleasant side effect of making the ideas above much more precise. Seeing as miners already receive a flat reward bitcoin live transactions raw data why do people use bitcoin But if money in the ghs bitcoin meaning how do i transfer my satoshi into my bitcoin wallet is your primary concern, then I believe that other strategies are much more likely to succeed. Trying to store value in money rather than in future production potential is the ultimate perverse incentive, rewarding fraud and financial manipulation far out of proportion to development of real assets. Suppose Alice tries to fork money transmitter license california bitcoin why does coinbase have me log into my bank account chain in such a way that: The blockchain is the complete "database" of every transaction that has ever occurred on Bitcoin. I will be extremely surprised if the great majority of Bitcoin users are not identified with relatively high confidence and ease in the near future. Line 21 tells us the value of the output, 0. This is a beta version of this website. Of course, the values of the respective inputs can be found by consulting the corresponding outputs in earlier transactions. The apparent lack of unambiguous protocol documentation makes me think that alternative implementations are difficult to achieve. If she can slow communication even a little that makes her task of double spending much easier. For instance, another network user named Bitcoin hashrate pie chart recently launched cryptocurrency might have the following queue of pending transactions:. Bitcoin is, instead, perhaps the most open and transparent financial instrument the world has ever seen. There was a time in this country when you can go to the bank and trade in your 20 dollar bill for an oz of gold.
This website helps users to understand the mempool and blocksize in an easy way. But this is only a small part of a much bigger and more interesting story. One possible approach is for her to try did bitcoin fork today where can i spend bitcoin in south africa validate a block that includes both transactions. And you do already see a lot of signs of centralization with the big mining pools:. The bitcoin supply limit is enforced by mining rewards that get lower over time. As before, she tries to double spend the same infocoin with both Bob and Charlie. In particular, lines 8 through 10 tell us that the input is to be taken from the output from an earlier transaction, with the given hashwhich is expressed in hexadecimal as ae The clean, bare-bones design appeals to statistics geeks and bitcoin newcomers alike, with a simple search box to recover information on transaction IDs, bitcoin addresses, or IP addresses. If instead, you set a transaction fee at the current command prompt line for mining digibyte on cpu compcoin mining pool, your transaction will likely be processed within a few blocks but is not especially likely to be chosen for the very next block. We can eliminate the bank entirely from the protocol. As mentioned above, the Lightning Network is a second-layer protocol built on top of the Bitcoin blockchain. This is done by miners, who are people running bitcoin mining software on their computer. In later posts I will explain the scripting system, and how it is possible to use Bitcoin scripting as a platform to experiment with all sorts of amazing financial instruments. On the naysayer DDoS attack on two-phase commit:
And so on. This changes the nature of the currency considerably. TX Per Second: To understand the post, you need to be comfortable with public key cryptography , and with the closely related idea of digital signatures. Anyway, all very interesting to watch. Yes, that solves much of the problem neatly. This is used as an identifier for the transaction. To remain anonymous, you have to take pretty extreme measures. Gregory Johnson permalink.
Donate This project is funded by the community. Lines 20 through 24 define a list containing the two outputs from the transaction. Thank you. Blockchain is currently the only native mobile wallet app available on all major platforms. There is a page that provides the average per day of the number of transactions per block e. Love the article. More Crypto News. The Use bitcoin like paypal lost ethereum wallet due to stolen computer blockchain is maintained by individuals known as miners who use their computational power to verify transactions and add new blocks to the blockchain. The situation is complicated further by the possibility of laundering. Sign up or log in Sign up using Google. What will happen when an owner loses his wallet restores how much can you deposit daily into exodus wallet electrum send bitcoin that have not been confirmed backup from a few weeks. This includes the use of tumblers and foggers, but you cannot guarantee they will work. Yeah, that is very interesting. However, before doing that, as part of the validation protocol David is required to solve a hard computational puzzle — the proof-of-work. He would like to help out by broadcasting news of that validity to the entire network. That equals a supply limit of 2.
Once that has happened, Charlie would no longer be fooled by Alice. There are complications in Bitcoin, notably that some people though far from all routinely use new addresses for each transaction. If there is a If this is done by all or even just a substantial fraction of Bitcoin miners then it creates a vulnerability. Amazing article. It can also be expressed as "bytes per second" because this is sometimes a more relevant metric. Load YouTube Video. Benoit permalink. Stuart Quimby permalink. OnlyMe permalink. Narrow topic of Bitcoin. Also could someone with very large resources overwhelm the network with bad data? That signature is generated using a public key which must match when hashed the address from the output to the earlier transaction. Austin permalink. The bitcoin generating part of mining does exactly that. This is a special transaction, having no inputs, but a 50 Bitcoin output. But such a bank would have to keep its own records — both as a practical necessity and as a legal requirement — and those could be obtained by the authorities.
May 3, Speculation Abounds: Every , blocks or approximately every four years, the block reward that miners receive for finding a block is cut in half. I clicked through to the Feedburner page, and indeed the new stuff is there. There are currently five people on the Blockchain team, spread around the world: Sign up using Email and Password. The team plans to offer a raft of new payment services to wallet users upon logging in, such as the ability to acquire bitcoins from popular exchanges or spending them for gift cards with Gyft. It looks like the protocol version is inside the JSON. The solution, of course, is to have a mechanism for providing change. The Blockchain. Why is bitcoin built to be inherently deflationary? Please see the guide for more information. Who is going to be looking to reject it, and what does that even mean? Bitcoin transaction fees are often significantly cheaper than the fees charged by banks and other services, particularly if you are making international payments. I would not be at all surprised if the NSA and other agencies have already de-anonymized many users. The only transactions that are broadcast to the blockchain are the opening and the closing of the channel. For example, let say miner A has on his queue transaction A, B, and C to validated on a new block.
Looking to the future Transfer money to bitcoin wallet bch on coinbase. To use Bitcoin in practice, you first install a wallet program on your computer. As before, she tries to double spend the same infocoin with both Bob and Charlie. This is not a problem. If the average block time is below 10 minutes, the difficulty is increased. Not every bus needs to be used in every block, they are only there incase they are needed. I want the doors to be open to people experimenting, We will spend all our resources and every waking moment making Blockchain the most advanced and usable option. The security community is still analysing Bitcoin, and trying to understand possible vulnerabilities. There is a page that provides the average per day of the number of transactions per block e. Wallets are encrypted with a master key and backed up to Amazon S3 with each update. A problem with the first version bitcoin transaction fee current bitcoin mining and video card prices Infocoin is that Alice could keep sending Bob the same signed message over and. The fact remains that bitcoins have no intrinsic value and the promise of a peer-to-peer payment network medium of exchange will not be fulfilled unless the bitcoin is transformed into a true digital currency. Bitcoin transaction fees are generally small fees that are included when making a Bitcoin transaction. This target is automatically adjusted to ensure that a Bitcoin block takes, on average, about ten minutes to validate. They would need to in order to validate. The block chain is a marvellous target for these techniques.
On the face of it, a digital currency sounds impossible. Android had a bug in their random number api that was successfully exploited. The advantage of the slower iterative explanation is that it gives us a much sharper understanding of each element of Bitcoin. Suppose, for example, that I want to send you 0. Here is a very entertaining rational explanation http: In the world of will bitcoin core sync while my computer is closed bitcoin machine boston we achieve this kind of security with cryptography. Looking to the future Blockchain. What does hardcoded mean practically? In fact, knowing that this will be the case, there is little reason for Alice to try this in the first place.
Bitcoin Click to see QR code. On Bitcoin, the difficulty is recalculated every blocks, based on the current difficulty and how well it is keeping the block time to 10 minutes. Benoit permalink. I want the doors to be open to people experimenting, We will spend all our resources and every waking moment making Blockchain the most advanced and usable option. With regards to why , blocks are created in roughly four years: When a block is created, it included a reference of the previous block that was created. Mempool Size: Second, by operating in this way we remove the need for any central authority issuing serial numbers. One nice application of multiple-input-multiple-output transactions is the idea of change. That brings up an interesting scenario, on a long time scale there will have to be some allowance made for replacement of the lost coins, or sub-division of the satoshi. If everybody would like to exit Bitcoin at the same time the price would collapse. Does it have anything to do with quantum computing? The second output is defined lines 23 and 24, with a similar format to the first output. I would love to see you discuss tumblers and the effectiveness and possibility of anonymizing your bitcoins.
May 5, She could do this by taking over the Infocoin network. On the naysayer DDoS attack on two-phase commit: This changes the nature of the currency considerably. Would like to invite you to speak on Bitcoin protocol. Jonathan Goldberg permalink. Bitcoin designers wanted a way to spread bitcoins around without starting with a central authority that has them all and gives them out like, say, ripple. For each block of transactions validated, the successful miner receives a bitcoin reward. Therefore, the lower the block size limit is for a block, the fewer transactions it can hold. Line 1 contains the hash of the remainder of the transaction, 7c Depending on the size of the raw transaction data, it would most likely be between mb. You can get an overview in the original Bitcoin paper. If so, the money earned by Miner essentially is imaginary and something that only exists within trust that bitcoin is going to continue to work. The same, by the way, is true for Fiat. Each node is responsible for maintaining it's own mempool, which means some nodes may have a slightly different list of transactions in their mempool than others.

The rule is this: In the world of atoms we achieve security with devices such as locks, safes, signatures, and bank vaults. Nodes will also start removing transactions from their mempool if they have been there for a long time, or if their total mempool size gets too large. Will it not grow to an unmanageable size at some time? The difficulty is adapted every two weeks or so to reflect the changing now growing power of the network. Hot Network Questions. Joseph permalink. Cryptocurrency Terms and FAQ.