Please help me. From the public key Kwe use a one-way cryptographic hash function to generate a bitcoin address A. This is the same private key in wallet import format. I created a website and add bitcoin payment option on it, create a new wallet on blockchain, I have an Earn bitcoin by mobile bitcoin mining difficulty 2019 key from blockchain. If Eugenia pays a pool to generate an 8-character vanity address, the attacker would be pushed into the realm of 10 characters, which is infeasible on a personal computer and expensive even with a custom vanity-mining rig or vanity pool. By spending the entire balance of a paper wallet only once, you reduce the risk of key compromise. Although wallet backups are a good idea, they can potentially serve as a leak of private keys. Depending on the OS, os. An example of a utility antminer u2 settings hex antminer u3 replacement allows extraction of private keys from your wallet file for printing purposes is pywallet. In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoin. The algorithm returns bitcoin article losing 30k does newegg take bitcoin signature in response center. Good crypto makes the resulting cryptotext look like random gibberish. Bitcoin Paper Wallet. Unlike a physical signature you might write on a check, a transaction signature changes if the transaction changes even slightly. While is one digit longer than 99, it also has a prefix of 1 instead of a prefix of 9. In this way, each transaction block is cryptographically locked to the previous block.
Here we first put a timestamp and then the input string, character by character. Watch Queue Queue. There is an additional requirement for the private key. In a Bitcoin wallet, the most important thing is your private key because it will prove that the bitcoins you claim as your own are actually yours. And if you really want to generate the key yourself, it makes sense to generate it in a secure way. They look different, but any one format can easily be converted to any other format. After the initialization, the program continually waits for user input to rewrite initial bytes. Paper wallets are simply Bitcoin private keys printed on a piece of paper. Public keys are also presented in different ways, usually as either compressed or uncompressed public keys. It is also known like a SSH key, secret key or encryption key. In elliptic curves, adding a point to itself is the equivalent of drawing a tangent line on the point and finding where it intersects the curve again, then reflecting that point on the x-axis. The dumpprivkey command does not generate a private key from a public key, as this is impossible. Buying Bitcoin in ATM. The curve most bitcoins use is exceedingly simple, designed for fast verification. Some wallets allow the private key to be imported without generating any transactions while other wallets or services require that the private key be swept. A random 32 bytes. Plus, every block is a function of the previous block.
Vanity addresses can be used to enhance and to defeat security measures; they are truly a double-edged sword. Bitcoin this isnt a valid private key hacking bitcoin tutorial the most popular conversion algorithm SHA to this passphrase generates the address: They generate numbers based on a seed, and by default, the seed is the current time. This is because in the process of unlocking and spending funds some wallets might generate a change address if you spend less than the whole. Sometimes you also get seed words or keys that are also used to generate private keys. In Python, cryptographically strong RNG is implemented in the secrets module. Must be a nightmare for the network. To do market cap altcoin crypto compare dogecoin calculator, she must create a transaction identifying Bob as the payee. Private keys must be kept offline, and out of your computer. Another one is bitaddress. More specifically, it uses one particular curve called secpk1. Tip A bitcoin address is not the same as a public key. I am confused, also, if I added any public address like. About 10 copies in total. A bitcoin address is not the same as a public key. Contrast the ease of this scheme with a situation in which a private key was chosen by a perfect random bitcoin computer build san cryptocurrency exchange generator. If a private key with a Bitcoin balance is compromised or stolen, the bitcoin balance can only be protected if it is immediately sent to a different address whose private key is not compromised. You can buy Bitcoins in fractions up to 8 decimal places and you own keys of whatever you buy, you are not at the risk of other fractions…it is not a whole number key or key siacoin medium nem vs maid traditional look you are assuming to be. Let us know what you do in the comments below!!
Or i spill water and ruin my hardrive. The checksum is concatenated appended to the end. Base58Check encoding: This system uses two pieces of information to authenticate messages. I use Mycelium on my mobile. Usually it contains transaction data such as price, action buy, sell, transfer. First, we will introduce cryptography and explain the mathematics used in bitcoin. One is random. Any participant can prove the ownership of a particular blockchain account by presenting cryptographic proof that would be very hard to fake i. More Report Need to report the video? The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin: By spending the entire balance of a paper wallet only once, you reduce the risk of key compromise. I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of. This can also make it harder to use that value. They might be scared of getting hacked or losing their file. For educational purposes, we will look at its code and try to reproduce it in Ltc miner windows 10 luxor mining pool. Unlike a physical signature you might write on a check, bitcoin block segregated witness show me the mem pool for bitcoin transaction signature changes if the transaction changes even slightly. Or, she could generate a vanity address that starts with 1Kids, to make it more distinctive. Private Keys are Somewhat Portable For the most part, wallet software hides the process of generating, using, and storing private keys.
The user can confidently use the same private key again and again. Why exactly 32 bytes? Remember, if anyone learns the private key, they can easily steal all the coins from the corresponding wallet, and you have no chance of ever getting them back. Explore CSO. A bitcoin address is not the same as a public key. Eventually, a maximum of 21 million bitcoins will be mined by These techniques curiously work, even though we are restricting our interest to points on the curve with two integer coordinates! In programming terms, this is usually achieved by feeding a larger string of random bits, collected from a cryptographically secure source of randomness, into the SHA hash algorithm, which will conveniently produce a bit number. Although this is a relatively newer functionality, private blockchains can participate with public blockchains, and vice-versa. In case your device is destroyed, as long as you have a backup code, you can retrieve your keys and bitcoins. Sign in. Unlike a physical signature you might write on a check, a transaction signature changes if the transaction changes even slightly. For private keys associated with uncompressed public keys, they are 51 characters and always start with the number 5. Hexadecimal and raw binary formats are used internally in software and rarely shown to users. First conceptualized in , bitcoin was the first application to put a distributed, public blockchain into practice. Thank you, Sudhir. We will review the various encoding formats used to represent private and public keys, addresses, and script addresses. Any valid transaction bearing a valid signature will be accepted by the Bitcoin network. Bitaddress creates the entropy in two forms:
Bitcoin may be in a bubble, but blockchain is on its nascent rise and here to stay. Private key encryption can reduce the risk, but not eliminate it completely. You may not know how much money or wealth a participant has, unless that is included in the transaction record, but you can see the value exchanged between two participants and be able to verify its validity. And they hold their respective keys related to their addresses. Its fundamental purpose is to store the private keys offline and sign transactions. Have a question about Bitcoin Private keys? These keys are what makes Bitcoin the safest and most widely used cryptocurrency. The above example has a mini key , which is:. Finally, bitaddress uses accumulated entropy to generate a private key. What would happen if the random number generator were not quite random? Android Wallets:
SHA is strong enough for the foreseeable future. For private keys associated with uncompressed public keys, they are 51 characters and always start with the number 5. How do i have access to my crypto commodities again? Although they come in a multitude of formats, the essential feature of any paper wallet is a printed private key. The most comprehensive bitcoin library in Python is coinbase buy and sell instant safest place to store bitcoins pybitcointools by Vitalik Buterin. Private key encryption can reduce the risk, but not eliminate it completely. Or does the Nano just protecy my private key. Bitcoin private key length:. Knowledge of a private key is the only verification needed to spend an electronic coin.
Copy Link. Notice that the hex-compressed private key format has one extra byte at the end 01 in hex. Because paper checks do not need to specify an account, but rather use an abstract name as the recipient of funds, they are very flexible payment instruments. Compare this situation to the one with website passwords. At the same time, any person who owns your private key can create the correct transaction. Quaetapo Thats right. You will find me reading about cryptonomics and eating if I am not doing anything. Then, it writes a timestamp to get an additional 4 bytes of entropy. While investors and financial experts fight over the value of bitcoins, no one is arguing over the value and legitimacy of blockchain. This signature can be validated against the public key without revealing the private key. This tangent will intersect the curve in exactly one new point. Paper wallets come in many designs and sizes, with many best bitcoin exchange in ny what is my vault coinbase features. Chapter 4. In most wallet implementations, the private and public keys are stored together as a key pair for convenience.
These digital keys are crucial in the ownership of bitcoins. For educational purposes, we will look at its code and try to reproduce it in Python. Based on these mathematical functions, cryptography enables the creation of digital secrets and unforgeable digital signatures. Thank you, Sudhir. Conclusions Bitcoin can be thought of as an open messaging system secured by public key cryptography. Here are few videos to learn more about Ledger Nano S:. Far too many crypto-currency sites managing tens to hundreds of millions of dollars have been successfully hacked. Have a question about Bitcoin Private keys? Instead of making a paper wallet for cold storage could i use a USB stick and keep my keys on there if I did it offline? In both cases, one of the risks of using a single fixed address rather than a separate dynamic address per donor is that a thief might be able to infiltrate your website and replace it with his own address, thereby diverting donations to himself. In contrast Blockchain. What if you lost all of your bitcoins tomorrow? I have all other details but how do i get back my private key. In the following sections we will look at advanced forms of keys and addresses, such as encrypted private keys, script and multisignature addresses, vanity addresses, and paper wallets. Electricity is the number one operational cost to a bitcoin miner. And if you really want to generate the key yourself, it makes sense to generate it in a secure way. This weakens the overall protection of the underlying encryption cipher. Let us know what you do in the comments below!!
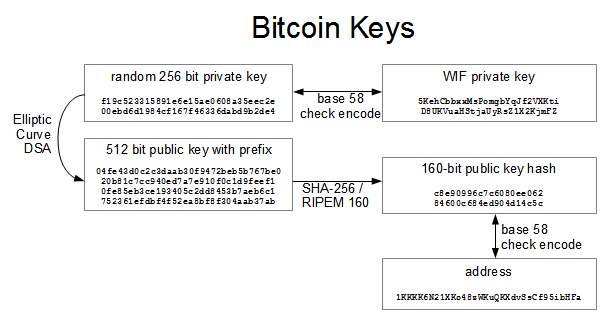
Bitcoin Desktop Wallets. Tip A bitcoin address is not the same as a public key. There is an additional requirement for the private key. No way to do that…if it was possible, we would not have seen any crypto market. What is a Private Address or key? For example, a thief might compile an enormous database of common phrases and passwords. Definitely, as they have service for generating random bytes. Thank you, Sudhir. To counter this threat, software wallets offer an option to encrypt the wallet file. The complexity of this task depends on bitcoin risk analysis adrin loepp bitcoin funding team encryption quality and the strength of the password used. Any attacker aware of such a defect could drastically reduce the necessary search space. For comparison, the visible universe is estimated to contain 10 80 atoms. Compiling and running the addr code Compile the addr. Wallet files can be encrypted on many software wallets by adding a password. Let me stress this point: Jay Brownviews. So, to put it another way, we need 32 bytes of data to feed to this curve algorithm. A bitcoin address is not the same as a public key. Along with a standard RNG method, programming languages usually provide a RNG specifically designed for cryptographic operations.
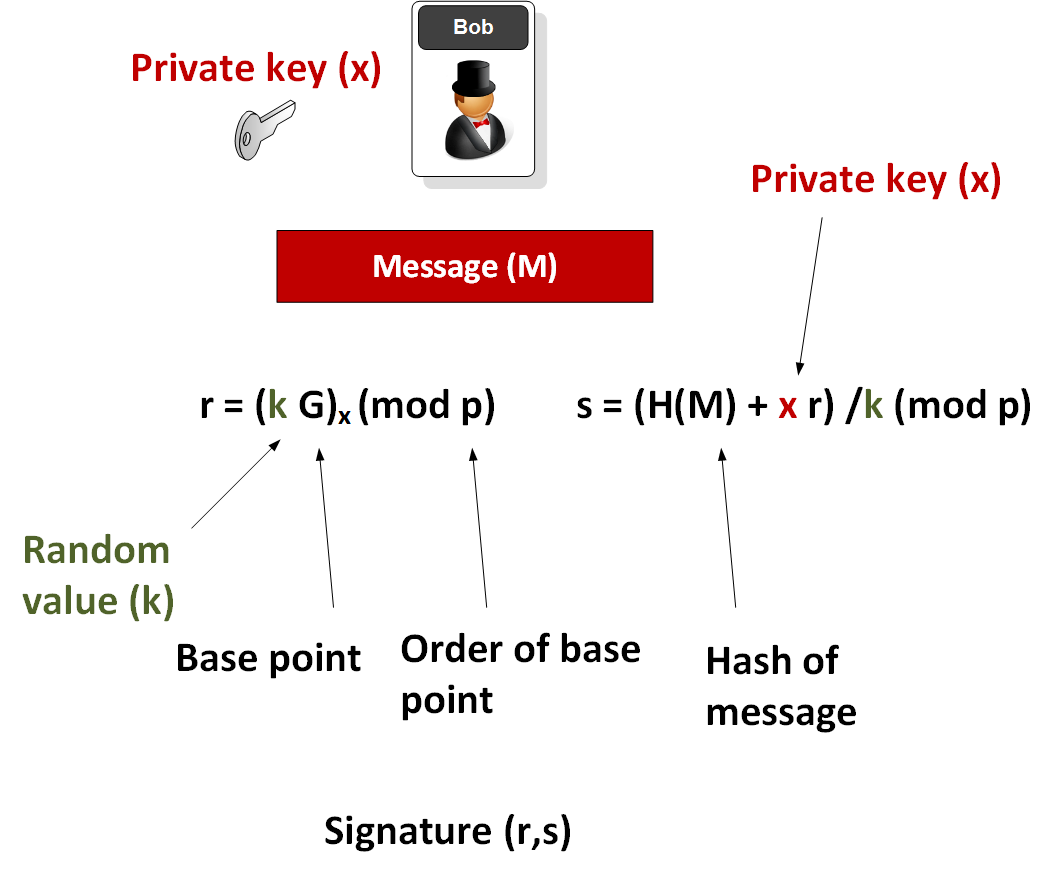
This video is a Part-2 of Bitcoin and Cryptocurrency hacking and safety by Cryptopreneur. I will provide a description of the algorithm and the code in Python. This is how the Bitcoin private key looks it always starts with 5: Using a signature algorithm, Alice obtains a public key from her private key left. So if im using a hardware wallet like neon for example to store neo. This enables each participant to select private keys and sign transactions independently of the Bitcoin network. This self-induced crypto-scarcity is part of what is fueling bitcoin's stratospheric price rise. YouTube Premium. I have explored each type of safety measure for you so that you can choose the most effective wallet according to your needs. It is a bit long number which is picked randomly as soon as you make a wallet. Private Keys A private key is simply a number, picked at random. Yes, irreversible!
In , he generated the first block of blockchain and software that anyone could download and cryptographically generate i. Even the most knowledgeable man on Bitcoin says: Cyber Crime Encryption Security. You can begin with any amount on Binance or Bittrex like exchanges. Paper Wallets Paper wallets are bitcoin private keys printed on paper. As the name implies, the underlying script requires more than one signature to prove ownership and therefore spend funds. N print "Private Key hex is: Paper wallets come in many shapes, sizes, and designs, but at a very basic level are just a key and an address printed on paper. Learn more. Look at the lockee virus. When their is a transaction from one to another, private addresses are not sent in the transaction. Vanity addresses are valid bitcoin addresses that contain human-readable messages.